In the past weeks I worked on UI Redressing exploitation methods. The UI Redressing Mayhem series is going to illustrate the results of my research, presenting 0day exploiting techniques and several vulnerabilities that involve high-profile web applications. Each post of the series will also provide detailed information about the vulnerabilities and techniques, together with working Proof-of-Concept exploits.
The following article will detail a previously unknown Mozilla Firefox vulnerability that affects the latest version (v.17.0.1) of the Mozilla web browser and allows malicious users to perform cross-domain extraction of sensitive data via UI Redressing vectors.
The following article will detail a previously unknown Mozilla Firefox vulnerability that affects the latest version (v.17.0.1) of the Mozilla web browser and allows malicious users to perform cross-domain extraction of sensitive data via UI Redressing vectors.
It was a dark and stormy night...
My security research on UI Redressing exploitation techniques grounds its roots in a web application penetration test where I was asked to exploit a UI Redressing bug with the explicit constraints to target Mozilla Firefox users. My objective was to achieve the cross-domain content extraction of an anti-CSRF token, in order to trigger the update of the victim's profile e-mail address: the powerful double drag&drop method was found to be appropriate in that context. To the best of my knowledge, the method was first introduced by Ahamed Nafeez and is based on the possibility to perform a drag&drop action between a framed web page, which displays the "sensitive" contents and is not protected by the X-Frame-Options header, and the framing page (the "dropper" page), which receives and stores the extracted content. The view-source handler is used here to bypass any framebusting code.
The main problem with my exploit development, during the penetration test, was that the drag&drop method was recently killed by Mozilla. An interesting solution to the Mozilla fix is the fake CAPTCHA method that was introduced by Krzysztof Kotowicz — and demonstrated to be effective against Facebook and Google eBookstore — but I chose the hard way and tried to bring the drag&drop method back to the masses: so please welcome the iframe-to-iframe cross-domain extraction method.
The iframe-to-iframe extraction method
The extraction method is extremely simple: instead of performing a drag&drop action of sensitive data, from a framed vulnerable web page to the framing one (attacker-controlled), the victim is tricked to visit a malicious html page that includes two iframes: the vulnerable page - where the sensitive content resides - and another attacker's page that is used to drop the extracted content (Figure 1). Firefox is not able to block this kind of attack because no check on cross-domain drag&drop between iframes is performed. As mentioned before, the method was tested against Mozilla Firefox version 17.0.1 - the latest stable release at the time of writing. The iframe-to-iframe technique was also tested against Google Chrome but the browser has been proved robust to the proposed attack.
 |
| Figure 1 - iframe-to-iframe d&d extraction method. |
All your LinkedIn accounts are belong to us
LinkedIn implements a stateless anti-CSRF mechanism that associates tokens to the HTTP requests that result in a change of the remote application state, such as the update of a user's profile information (e.g. job title or the login e-mail address). A stateless anti-CSRF method is generally based on a secret token, delivered as a cookie parameter, and a token which is included in every state-changing HTTP request: the remote web application considers as genuine exclusively the HTTP requests that have the same token value for both the cookie and HTTP parameter. Otherwise, a request is considered untrusted and it is not computed. The LinkedIn's anti-CSRF mechanism involves a cookie parameter called JSESSIONID and an HTTP parameter named csrfToken in order to store the secret tokens (Figure 2). A stateless mechanism can be easily bypassed with well known web hacking techniques.
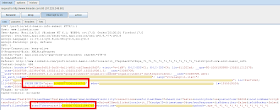 |
| Figure 2 - anti-CSRF tokens. |
- http://www.linkedin.com/companies?trk=hb_tab_compy
 |
| Figure 3 - Vulnerable LinkedIn web resource. |
The vulnerability can be easily abused to craft a UI Redressing exploit that triggers the victim to drag&drop the anti-CSRF token. The token can then be abused to edit any information on the victim's profile and even to reset the account password. In order to demonstrate the effectiveness of the attack I developed a fully working Proof of Concept exploit that adds the attacker's e-mail as a trusted address to the victim's profile and verifies the e-mail itself. At that point, the attacker can easily reset the victim's password using LinkedIn password reset mechanism.
The following are the logical steps implemented by the Proof of Concept exploit:
- The malicious page frames both the LinkedIn vulnerable page and the attacker-controlled "dropper" page;
- The malicious page allows the victim to play the d&d game, which extracts the anti-CSRF token;
- The malicious page can now bypass the anti-CSRF protection and adds a new e-mail address to the victim's profile. The action involves the forwarding of a confirmation e-mail from LinkedIn system to the attacker box: an activation URL is included;
- The exploit interacts with an attacker's script — /linkedin/linkedin.php — which accesses the attacker's mail box via IMAP and waits for the Linkedin activation e-mail. Once obtained the e-mail, the URL is returned back to the malicious page, which is still loaded by victim's web browser;
- The script can now simulate the navigation of the fetched URL in order to confirm the new address.
The attacker can now reset the victim's account password abusing the password reset functionality, where he will type the e-mail address previously added to the targeted profile. Figure 4 highlights the different HTTP requests exchanged between the attacked web browser, the attacker's servers and the LinkedIn web application, in order to achieve the password resetting.
A working PoC has been developed and can be downloaded here. The following is a video of the attack:
LinkedIn Team was informed about this attack scenario. The following are a series of suggestions that should prevent this kind of attacks:
 |
| Figure 4 - Sequence diagram detailing the attack. |
Beyond the Mayhem
LinkedIn Team was informed about this attack scenario. The following are a series of suggestions that should prevent this kind of attacks:
- Protect every web resource that includes anti-CSRF tokens with the X-Frame-Options header. Nowadays, this mechanism is available in all major browsers;
- Consider to adopt a stateful anti-CSRF mechanism that should not perform the validation on the basis of potentially attacker-controlled inputs.
Nice catch. Do you think exploiting cross-iframe same-domain drag&drop might be plausible?
ReplyDeleteI started a write up about this in Feb last year. This is the link to the notes i collected:
ReplyDeletehttps://docs.google.com/open?id=0B3NJm1mhSs7TNkRyRmdCYlQ4MEE
I never got around to an actual write up but
http://m-austin.com/tools/drag2.html and
http://m-austin.com/tools/drag3.html are some demos.
Using links with CSRF or session ids also works well. Also facebook plugins with the user photo / link like facebook comments also works well.
Albino, I didn't investigate, yet.
ReplyDeleteMatt, I appreciate your notes even if I can't find a previously published paper/article about the techniques I described so.. I hope you enjoyed the formalization of the issue and the publication of the "method"!
Oh I enjoyed the writeup just upset at my self for being lazy. ;) Great write up!
ReplyDelete